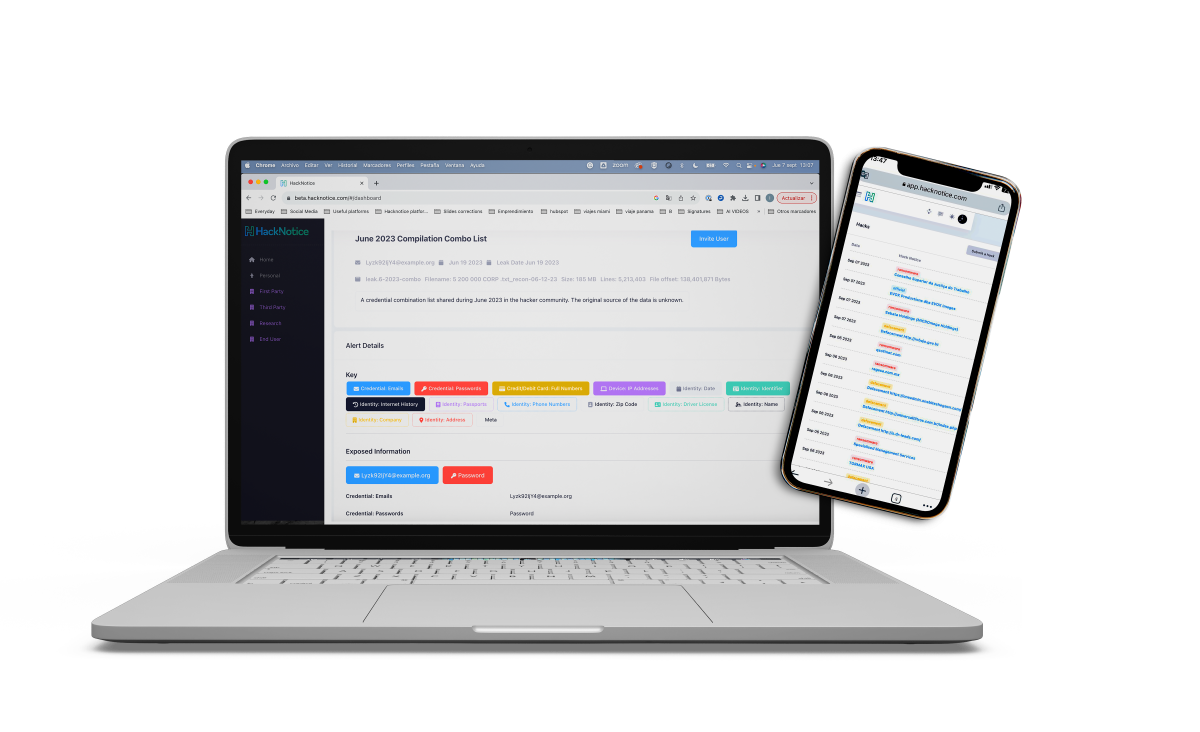
HackNotice instantly arms your security team with actionable, real-time intelligence on dark web and supply chain threats — seamlessly integrated into your workflows.
Upcoming Event
Join HackNotice and Pentera for a live fireside chat on July 30 as we break down how to turn leaked credential alerts into real, actionable defense strategies. Learn how to cut through alert fatigue, validate identity risks with breach simulations, and take back control of your organization’s exposure.
Key Takeaways include:
Upcoming Event
Global Cyber Siege: Ransomware & Breach Trends in 2024
Cyber Threats: 2024 Unpacked
Explore the radical shifts in 2024's ransomware and data breach landscape, uncovering new attacker tactics and the rise of aggressive gangs. This video dissects new attacker tactics, the rise of aggressive cybercriminal gangs, and highlights how data exfiltration has become a primary weapon in the ongoing digital battle.

HackNotice is a leading dark web threat intelligence platform that helps organizations identify, understand, and act on digital risks across their entire ecosystem — employees, vendors, and customers. With real-time monitoring, customizable alerting, and deep visibility into breached and trafficked data, HackNotice makes it simple for security teams to proactively prevent attacks, respond faster to incidents, and reduce overall risk exposure. From infostealer malware detection to third-party compromise alerts, HackNotice delivers tailored insights that drive action — all through a unified, scalable platform built for modern threat defense.

HackNotice delivers proactive, modular solutions that align with your goals and grow with your needs. Choose the services that matter most, integrate seamlessly into your workflows, and rely on our expert support every step of the way
HackNotice delivers end-to-end dark web threat coverage — from third-party breaches and ransomware to individual exposed credentials, executive PII, and sensitive data (financial data, API keys, etc.). With modular services and built-in investigation tools, you get the visibility and speed to act across your entire risk surface.
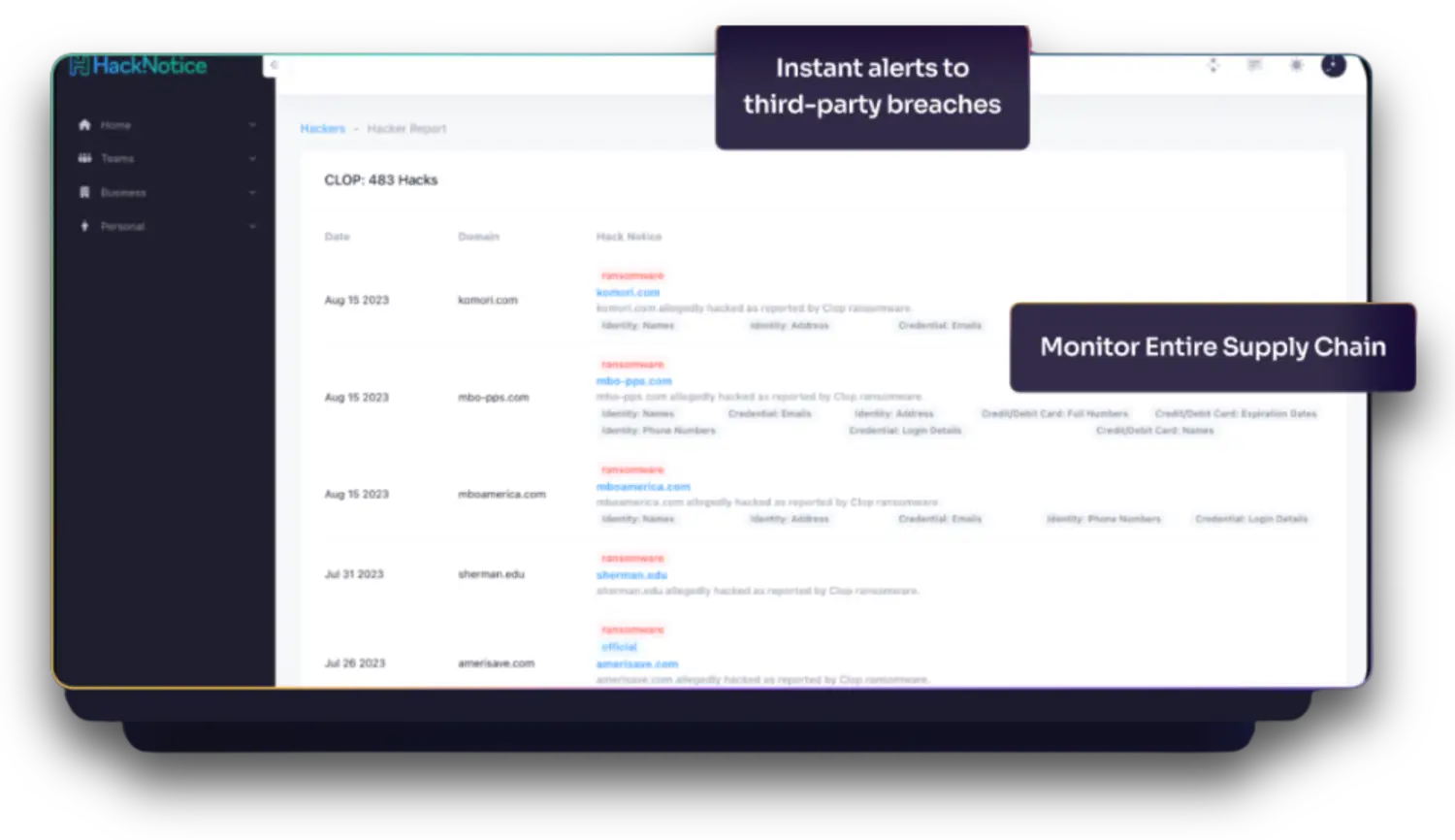
HackNotice’s Third Party Threat Management service provides continuous, real-time cybersecurity monitoring of your entire supply chain, proactively identifying data breach threats and dark web exposure levels within your extended business ecosystem.
Early Detection and Rapid Response
Time to knowledge is critical with third-party incidents. Learn about breaches to your supply chain in real-time, allowing for faster incident response to mitigate potential damages.
Improve Vendor Reviews & Onboarding
Don’t rely solely on vendor questionnaires. Receive direct insights into vendor risk profiles and breach histories for any company, ensuring compliance and defense against third-party risks.
Customized Alerting Tailored To You
Reduce alert fatigue and wasted time by only being notified of actionable events. Tailor your alerts and workflows based on vendor criticality, event types, and more.
Uncover Fourth-Party Risks
Stop the domino effect. Extend risk monitoring beyond direct partners to include the vendors of your vendors, revealing hidden incidents within your extended supply chain.
In-Depth Data Breach Investigations &
Reporting
In-Depth Data Breach Investigations & Reporting
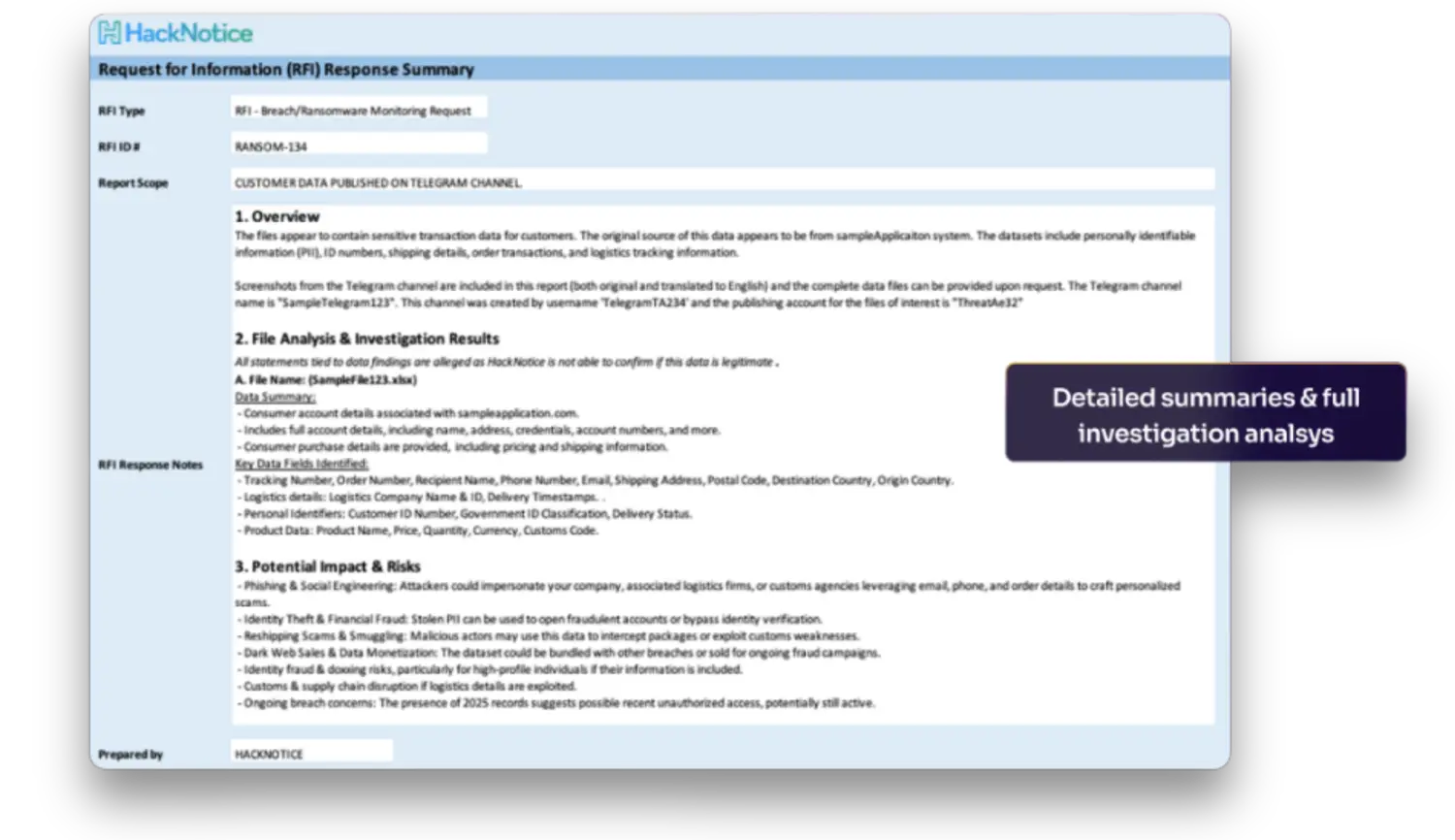
HackNotice’s Dark Web Incident Analysis service empowers your team with in- depth investigations and ongoing monitoring of cyber incidents affecting your organization or supply chain.
Powerful Executive Summaries
Receive a comprehensive summary of the breach, threat actor communications, ransomware events, and any associated compromised data.
Visual Evidence & Raw Data Breach Files
Gain full visibility into compromised data, including screenshots of dark web postings and verified breach components.
Detailed Investigation Report
Complete analysis of technical findings, compromised data, associated threat actors/ransomware gangs, and other potentially affected entities.
Supply Chain Threat Insights
Investigate vendor, partner, and third-party compromises to mitigate risks and stay ahead of interconnected breaches.
Comprehensive Monitoring of Key Dark Web Forums and Channels
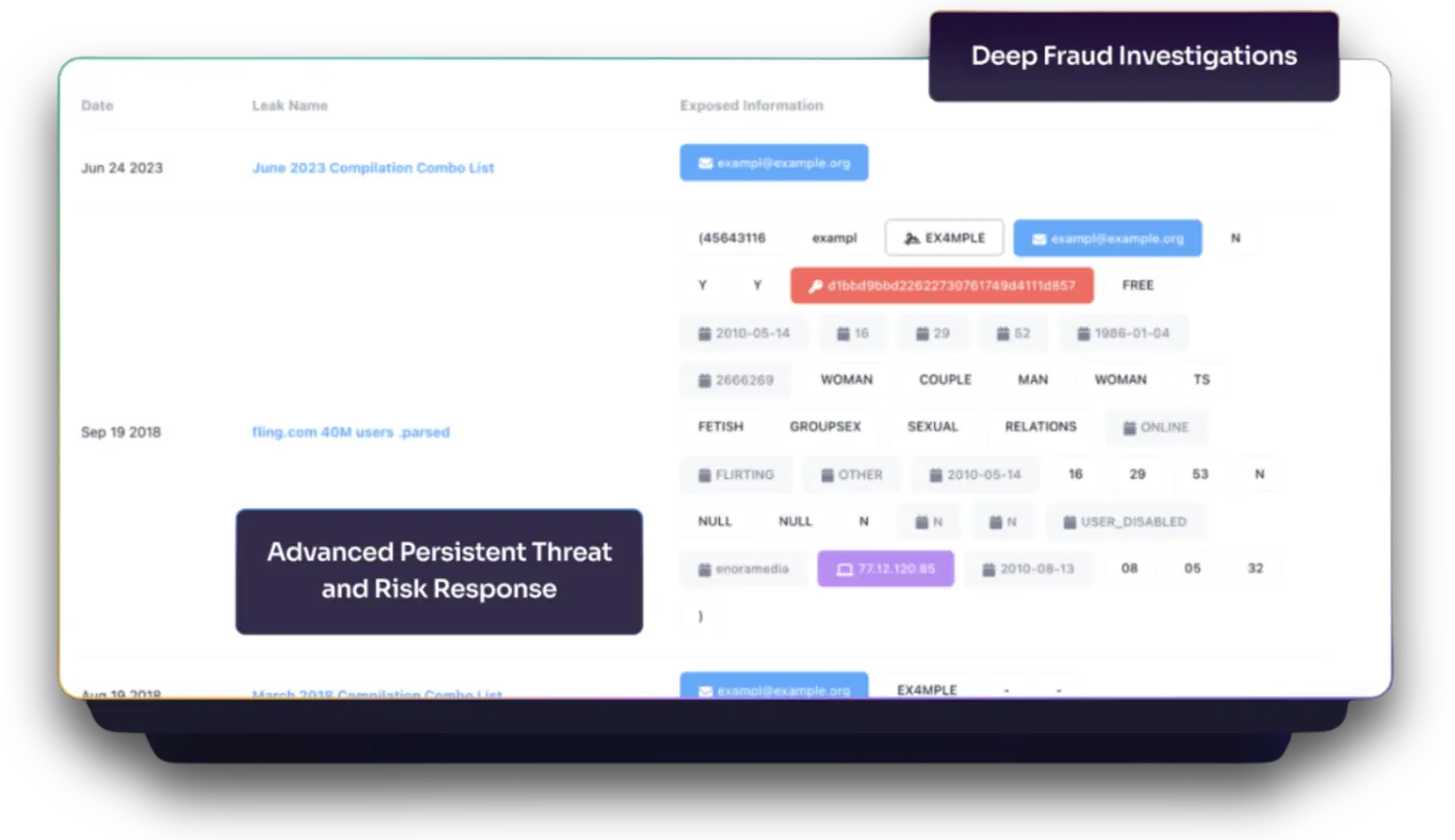
HackNotice's Continuous Dark Web Monitoring service scans your digital footprint 24/7 to detect compromised credentials, data leaks, and threats like infostealer malware. It alerts teams to employee exposures from credential dumps or third-party breaches, enabling quick response before exploitation. Customizable alerts reduce noise while protecting against account takeovers (ATO) and social engineering.
Accelerate Reaction Time
Rapidly detect exposed passwords and data tied to any email address, username, and more. Boost your ability to respond to threats rapidly with around-the-clock real time alerting.
Protect Your Customer & Vendor Accounts
Protect against dark web threats outside of your own walls. Monitor for exposed credentials tied to your customer’s and/or vendor’s accounts to mitigate unauthorized access.
Full-Spectrum Dark Web Executive Protection
Protect your highest-value targets. Get alerts on any exposed sensitive data linked to any of their accounts, usernames, phone numbers, and more.
Minimize Wasteful Alert Fatigue
Only receive alerts for data you care about. Utilize our customizable alerts to tailor your own workflows based on data types, severity, and recency.
Infostealer detection, compromised credentials, PII, and more
HackNotice’s Trafficked Dark Web Data Services continuously scans the dark web for compromised credentials, enabling your organization to proactively protect your customers, vendors, and executives helps safeguard their accounts and minimize business risk. Additionally, tracking leaked critical data strings like API keys, authentication tokens, and account numbers helps prevent unauthorized access to sensitive systems and information.
Stay Ahead of Account Take Over (ATO)
Proactively detect and prevent account takeovers by continuously monitoring compromised credentials, malware-infected endpoints, and early indicators of cyber-attacks.
Identify Top Risk Corporate Emails
Prioritize monitoring to swiftly detect and respond to potential malware components, significantly reducing your vulnerability to account takeovers and social engineering threats.
Identify Social Engineering Risks
Utilize metadata analysis to reveal early indicators of social engineering attacks, enabling your team to recognize threats early and take preemptive action against targeted exploits.
Relevant, Actionable Insights
Receive timely, prioritized alerts tailored to your organization’s specific criteria to minimize alert noise, streamlined into your existing security workflows.
Infostealer malware is now one of the fastest-growing threats online—quietly stealing credentials from infected devices and flooding the dark web with login data. These stolen records often include usernames, passwords, browser sessions, and corporate access points—well before a breach is ever detected.
Why it matters:
HackNotice detects these exposures in real time so you can take action before attackers do.
Check if Your Business Email Has Been Exposed By Infostealer Malware
Enter your business email to see if it’s linked to infostealer data on the dark web – free and instant.
instant infostealer check request via email address
Private. Secure. No login required.
Prefer to Check Your Entire Corporate Domain Instead?
Request a full dark web report on your company’s domain to see all recent dark web trafficked data, detected historical data breaches, and your Threat Factor rating.
Complete the form and we’ll reach out.
2025 HackNotice. All rights reserved.
Contact Us
Complete the form and we’ll reach out.
Prove It or Lose It
Validating Identity Threats Before Attackers Do
Reserve Your Spot Today!